SSO Technical Requirements
Technical Requirements Overview
Single Sign-On (SSO) allows a third-party to authenticate a user prior to granting access to the Qualtrics System. Qualtrics supports four types of SSO authentication: Google OAuth 2.0, Central Authentication Service (CAS), Lightweight Directory Access Protocol (LDAP), and Security Assertion Markup Language (SAML). Each type requires the third-party to have a specific type of server. For example, CAS SSO authentication relies on the third-party having a CAS server.
This page covers the technical requirements you must meet. These settings must be configured with your IT team and then communicated to the Qualtrics SSO support team.
Google OAuth 2.0
Google OAuth 2.0 is an authorization framework that can be used to authenticate users into the Qualtrics platform. To configure Google OAuth 2.0 for third-party authentication, users who will access the platform must have a Google account.
The following configuration parameters must be provided:
- Valid Email Domains
- Specific email domains are required to authenticate users’ email addresses against on each login attempt.
Qualtrics only receives the email associated with users’ Google accounts when authenticating against Google OAuth 2.0. The email is used to populate the Qualtrics Username, First Name, Last Name, and Email Address fields.
Once the desired Valid Email Domains are provided, Qualtrics can arrange to set up a Google OAuth 2.0 integration with the third-party.
Lightweight Directory Access Protocol (LDAP)
Lightweight Directory Access Protocol (LDAP) is a directory service against which a third-party can authenticate. Qualtrics can be set up to automatically authenticate against an LDAP server when a user attempts to login to the Qualtrics platform. To set up an LDAP integration, it is assumed that the third-party has a working LDAPv3 server.
The following configuration parameters must be provided:
- LDAP Server Hostname: IP Address or name of server.
- LDAP Server Port: Port Qualtrics will use to communicate with the server.
- Base Distinguished Name (DN): For example:
o=organization - Bind Distinguished Name: Search based Bind DN or Bind DN user. This is not required if the LDAP server allows unauthenticated searches.
- Bind Password: This is not required if the LDAP server allows unauthenticated searches.
- Authentication filter parameters: For example:
uid=%username% - Logout Redirect URL: Qualtrics requires a Logout Redirect URL to clear users’ login sessions on logout. If no Logout Redirect URL is provided, Qualtrics can redirect users to https://qualtrics.com, or another URL of your choice. However, it will not clear users’ login session, and users will be able to log back in immediately by clicking the back button or returning to the login page.
- LDAP Attributes
- Required:
- Email Address Field attribute (e.g., mail)
Qtip: This attribute must contain values in the format of an email address. For example, value@email.com.
- Email Address Field attribute (e.g., mail)
- Optional:
- First Name Field attribute (e.g., firstname)
- Last Name Field attribute (e.g., sn)
- User Type Mapping attribute
- Division Mapping attribute
- Group Mapping attribute
- CX Dashboards metadata attribute(s)
- CX Dashboards Automatic Role Enrollment attribute(s)
- Required:
Once the above information is provided, Qualtrics can arrange to set up a LDAP integration with the third-party.
Central Authentication Service (CAS)
Central Authentication Service (CAS) provides enterprise single sign-on service and is supported by the JA-SIG CAS. More information about CAS can be found at https://www.apereo.org/projects/cas. The Qualtrics System can act as a CAS client, allowing the user to authenticate via CAS and login to the Qualtrics system. To setup CAS SSO, it is assumed that the third-party has a working CAS server using the CAS 2.0 protocol or newer.
The following configuration parameters must be provided:
- CAS Server Hostname: Name of server.
- CAS Server Port: Port Qualtrics will use to communicate with the server.
- URI to the CAS System on the Host
- Logout Redirect URL: Qualtrics requires a Logout Redirect URL to clear users’ login sessions on logout. If no Logout Redirect URL is provided, Qualtrics can redirect users to https://qualtrics.com or another URL of your choice. However, it will not clear users’ login session and users will be able to log back in immediately by clicking the back button or going to the login page again.
The following parameters vary based on whether or not you’re using a version of CAS that supports SAML 1.1.
- If SAML 1.1 is not supported: The CAS username will be used to populate the Qualtrics username, email address, first name, and last name fields.
- If SAML 1.1 is supported: The following configuration parameters must also be provided:
- Required:
- Email Address Field attribute (e.g., mail)
Qtip: This attribute must contain values in the format of an email address. For example, value@email.com.
- Email Address Field attribute (e.g., mail)
- Optional:
- First Name Field attribute (e.g., firstname)
- Last Name Field attribute (e.g., sn)
- User Type Mapping attribute
- Division Mapping attribute
- Group Mapping attribute
- CX Dashboards metadata attribute(s)
- CX Dashboards Automatic Role Enrollment attribute(s)
- Required:
Once the above information is provided, Qualtrics can arrange to set up CAS integration with the third-party.
Security Assertion Markup Language (SAML)
Security Assertion Markup Language (SAML) is an XML-based standard for exchanging authentication and authorization data between security domains, or an Identity Provider (a producer of assertions) and a Service Provider (a consumer of assertions). The Qualtrics System can be set up to automatically authenticate through a third-party Identity Provider (IdP) using SAML when a user logs into the Qualtrics System. To set up a SAML integration, it is assumed that the third-party has a working SAML 2.0, or Shibboleth 2.0 implementation, and can support Service Provider (SP) initiated logins.
Qualtrics supports both IdP and SP-initiated workflows for SAML logins. The more common of the two is an SP-initiated exchange, whereby users begin the flow at https://brandID.datacenter.qualtrics.com, or their organization’s Vanity URL. The IdP-initiated exchange is primarily used when users authenticate on an internal network, whereby users begin the flow at an internal application portal.
The following configuration parameters must then be provided:
- Identity Provider (IdP) Metadata (in XML format as a link or an attachment)
- Required tags:
- EntityDescriptor
- KeyDescriptor
- SingleSignOnService
- Both HTTP Post and HTTP Redirect bindings within the SingleSignOnService are supported. HTTP Post must be used, though, if you require our AuthnRequest to be signed.
- SingleLogoutService
- This field is used to redirect users to a URL that will clear users’ login sessions on logout. If no SingleLogoutService URL is provided, Qualtrics can redirect users to https://qualtrics.com or another URL of your choice. However, it will not clear users’ login session and users will be able to log back in immediately by clicking the back button or going to the login page again.
- Required tags:
- SAML Attributes
- Required:
- Username Field attribute (i.e. samAccountName)
- The attribute must contain values that are unique, unchanging, and not confidential.
- Email Address Field attribute (e.g., mail)
Qtip: This attribute must contain values in the format of an email address. For example, value@email.com.
- Username Field attribute (i.e. samAccountName)
- Optional:
-
- First Name Field attribute (e.g. firstname)
- Last Name Field attribute (e.g. sn)
- User Type Mapping attribute
- Division Mapping attribute
- Group Mapping attribute
- CX Dashboards metadata attribute(s)
-
- Required:
Once the above information is provided, Qualtrics can arrange to set up a Shibboleth/SAML integration with the third-party.
How to Get and Decrypt a SAML Response
A SAML response is sent by the Identity Provider to the Service Provider after successful SAML authentication. The SAML response contains all the information passed from the Identity Provider such as attributes, certificates, bindings, etc. This information is valuable when troubleshooting any issues with authorization or throughout the login process.
There are many tools available to aid in obtaining a SAML response. Below is a method that should be available in most browsers, but feel free to use any method.
- Open a new tab in your browser.
- Open the Developer Tools.
Qtip: These may be located in different locations depending on the browser being used. The screenshots on this page reference the look and feel of a Chrome browser.
- Choose the Network tab.
- Select Preserve Log.
- Enter the login URL into this browser tab and login via SSO.
- Under Name, you’ll want to select the item that says “default-sp”.
- Under Headers, towards the bottom under Form Headers you’ll see a block of characters labeled SAML response.
Qtip: If our support team has requested a SAML response, you can stop at this step.
- The SAML response is currently Base64 encoded. To decode the SAML response into a readable format, you can use any Base64 decoder found online.
Qtip: Check out these tools for encoding base64 and decoding base64.
How to read a SAML response
There are a few key pieces of information in a SAML response that can help you troubleshoot.
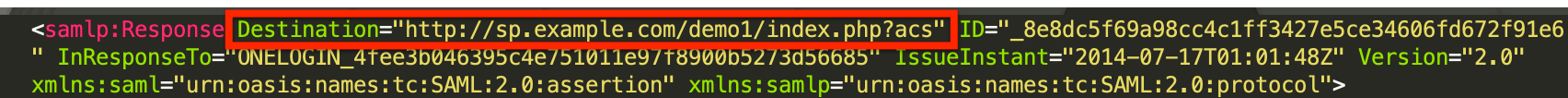
- Destination: This corresponds to the Service Provider Assertion Consumer Service URL and is generally found near the top of the SAML response.
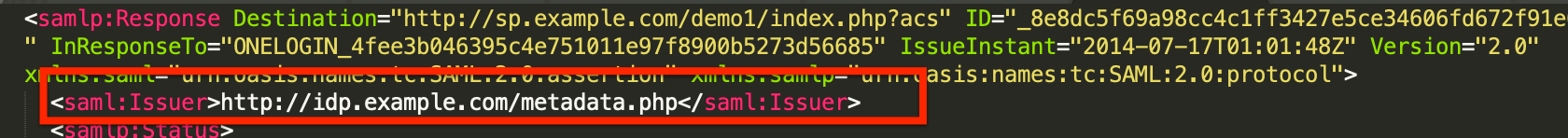
- Issuer: This corresponds to the Identity Provider Entity ID and is generally found near the top of the SAML response.
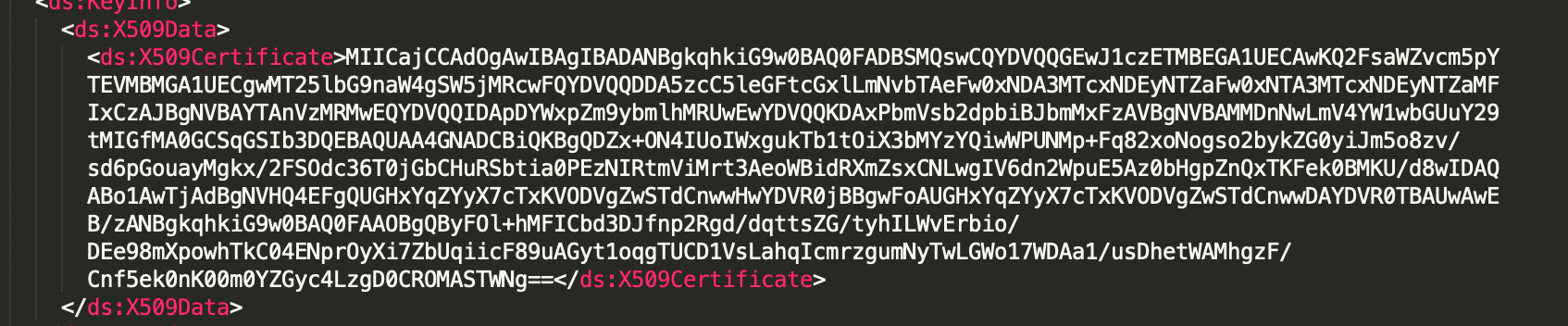
- X509Certificate: This corresponds to the Identity Provider signing certificate and is generally found in the middle of the SAML response.
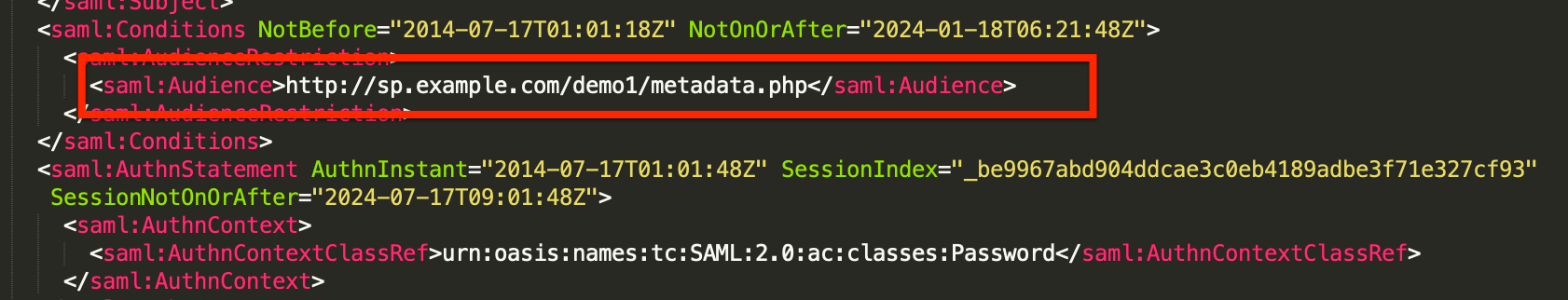
- Audience: This corresponds to the Service Provider Entity ID and is generally found in the middle of the SAML response.
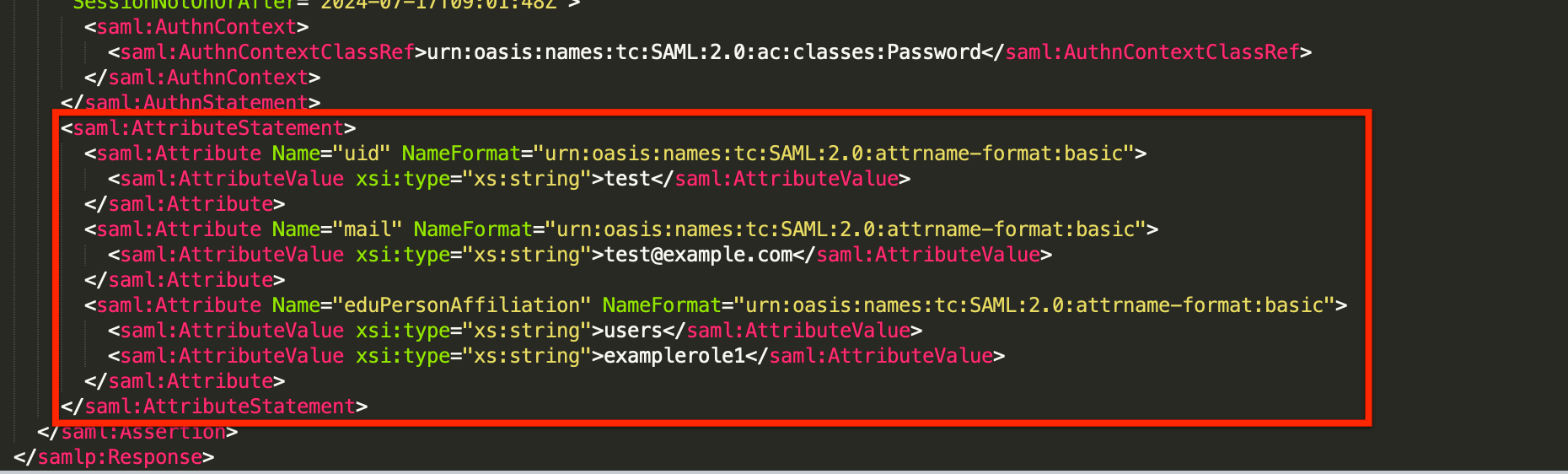
- Attribute Statement: This contains all the attribute names and values being sent by the Identity Provider and is generally found at the bottom of the SAML response.