Data Isolation
About Data Isolation
Qualtrics’ most important concern is the protection of customer data. We protect our servers using Akamai’s Cloud Security Suite and high-end firewall systems. We regularly perform scans and penetration tests to ensure that any vulnerabilities are quickly found and patched, and we only allow trusted data centers, independently audited using the industry standard SSAE16 method, to host our services.
For customers with even more stringent security needs, Qualtrics offers Data Isolation, which takes our world-class security one step further by offering an extra layer of data encryption.
Acquiring Data Isolation
Data Isolation is available for all licenses. If you are interested in purchasing it or learning more, talk to your Account Executive or Account Services.
Note that you can only purchase access to Data Isolation for a whole brand, not just one account, and that you must be a Brand Administrator to ask for this feature. After Data Isolation is enabled, it cannot be disabled for the brand.
Encryption Methods
Qualtrics Data Isolation has separate processes for the collection of data and for the access of data.
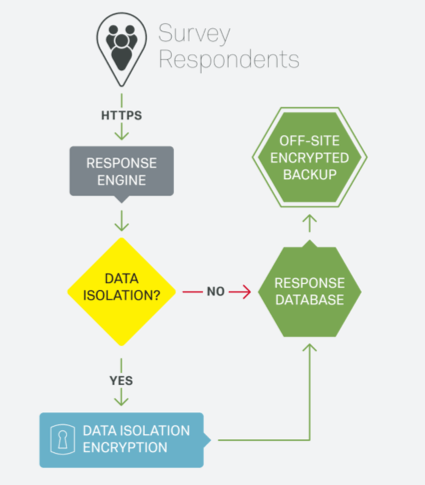
Encrypting Response Collection
- A respondent takes a survey and the response is submitted to Qualtrics short-term response storage over HTTPS.
- The unique customer ID for the survey is referenced to determine whether or not the
customer uses Qualtrics Data Isolation. If the customer uses Data Isolation, all data for every survey collected by that customer are encrypted. - If Data Isolation is used, the Encryption Service uses the customer-specific Master Key in Amazon KMS service to retrieve the survey’s AES 256-bit data encryption key from the Amazon Key Management Service.
- The Encryption Service uses the key, plus a response-specific initialization vector, to encrypt the data and write it to the Qualtrics Response Database.
- When the response information is eventually recorded to backup in an offsite data center, backup data are still in its encrypted form and an extra layer of encryption is applied to the entire disc.
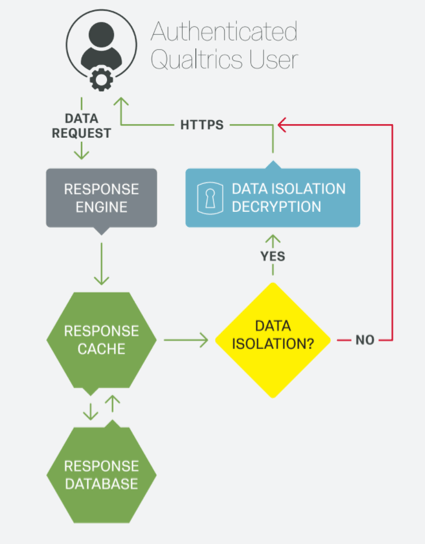
Encrypting Data Access
- The user authenticates to Qualtrics.
- The user makes a request to response storage to get data for a particular survey.
- The unique customer ID for the survey is referenced to determine whether or not the customer uses Qualtrics Data Isolation.
- If Data Isolation is used, the Encryption Service uses the customer-specific Master Key in Amazon KMS service to retrieve the survey’s AES 256-bit data encryption key from the Amazon Key Management Service.
- The encrypted data are retrieved from the Qualtrics Response Cache and/or Response Database and then decrypted with the customer’s key and the response’s unique initialization vector.
- The data are returned in plaintext to the user over HTTPS.
Highlights, Specs, and Benefits
Here are some of the features you can expect from Qualtrics Data Isolation:
- Advanced Encryption Standard (AES) 256-bit encryption (14 cycles of repetition)
- Symmetric Key is encrypted using Master and Data
- Encryption Keys through by Amazon KMS
- Data are encrypted when stored in a database
- Customer specific encryption keys are unique
- Each survey has a unique Initialization Vector (IV). We use IVs per survey to preserve important product functionality, such as filtering.
- Off-site backups are double encrypted
- Full audit trail for all accesses to customer encryption key
- Although the persistence service is a multi-tenant solution, the data are encrypted at rest and can only be decrypted by an authenticated internal service. Even physical access to the disk does not represent
a security risk to the customer
Data Isolation Limitations
While the majority of features work the same for brands with and without Data Isolation, there are features that have different levels of support or limitations. We work hard to ensure that Data Isolation brands have equivalent features, but the nature of individual record encryption limits the availability of a few features:
Degradation
Some features are enabled on data isolated brands but degrade in functionality. For example, some parts of the platform will only support full string searches rather than substring searches. The list of limitations below will degrade in functionality but will be partially supported on data isolated brands:
- Substring Searches: “Contains” keyword searches do not support substring matches (i.e. partial words) when searching text responses. This includes “contains” searches in filtering data, reports, and CX dashboards as well as “contains” searches launched by clicking on a word cloud widget. Substring searches for contacts in the XM Directory are not supported if your brand has data isolation. Additionally, substring searches for users when sharing a Web / App Feedback project is not supported. Substring searches and transcript search in the Audio & Video Editor are not supported if your brand has data isolation.
Qtip: For example, if you have a text response that reads, “Qualtrics is the best company!” the keywords “Qualtrics” and “company” are supported while the substring “Qual” is not.Qtip: If you’re searching for a field in your XM Directory that has multiple words in its name or field values, you will need to search by the full field name or value. For example, if you want to find the Embedded Data field “Company Name” in your directory, you need to enter the entire field name. If you search just “Company” or just “Name”, you will not see “Company Name” in your search results. Similarly, if you’re filtering for the contact with the first name “Sara Ann”, you will need to enter “Sara Ann” for her to appear in your results; searching by just “Sara” or just “Ann” will not display the contact you’re looking for.
- Non-Numeric Fields Sorting: Many widgets and data visualizations allow you to sort your data based on certain criteria (i.e. A-Z sorting). Data Isolation fields do not allow you to sort by non-numeric fields.
Qtip: You’ll be able to sort by fields that are in a numeric format, which includes fields saved as a Numeric Value, Number Set, or Date. Read the Field Types section for more information on field types.
- Number and Date Conditions: Embedded data fields cannot be used in number or date conditions when filtering data, searching contacts, or creating segments in XM Directory. The full list of unsupported conditions are:
- Number: Greater than / Less than / Greater than or equal / Less than or equal
- Date: On or after / Before / Between / In the past / In the next
Opt-in Features
The following features are disabled by default. You can enable this feature, but the data will not be data isolated:
- Comment Translation: Since comments are sent to a third-party for processing, these features are disabled by default on Data Isolation brands. However, they can be enabled by turning on Allow Third Party Comment Translations in the brand’s Organization Settings.
- EDGE Data Scrubbing Services: If you have contracted Qualtrics EDGE to perform data scrubbing on your behalf, that data will not be isolated while being scrubbed.
Unavailable Features
Not all features are available for data isolated brands. Features that can’t be enabled include:
- Action Planning: Action planning for CX and EX is currently not supported by Data Isolation.
- Frontline Feedback: Frontline Feedback is not currently supported by Data Isolation.
- Supplemental Data Sources: Supplemental data sources are not supported by Data Isolation.
- Location Selector Question: The location selector question is not supported by Data Isolation.
Guidance and Other Limitations
This section contains guidance on using certain features in data isolated brands and covers some additional limitations.
- Guidance on emails and all messages: When writing emails or saving messages in the library to use later, make sure never to type out identifying information. Instead, always use piped text for identifying information.
- Impact on Performance: Since Data Isolation adds an extra layer of encryption to your data, there is additional processing time that needs to be taken into consideration when displaying data. You may notice that your dashboards take more time to load, and this is due to the extra step of decrypting the data before it can be displayed.
- Employee Experience projects: Employee Experience projects have a few unique Data Isolation limitations in addition to the other ones listed in this section:
- You may upload participants without a value for email, provided they have a unique identifier.
- Per the substring search limitation above, you cannot search by substrings anywhere in EX projects (participants tab, dashboard and widget filters, messages tab, etc).
- Enhanced Anonymity for Org Hierarchies is not supported yet. (This feature is still in preview. However, the features of Enhanced Anonymity that are generally available and documented on our support page are compatible with Data Isolation.)
- The names of participant metadata fields are not encrypted, but their values are.
- 360 Projects: In addition to the above Employee Experience limitations, 360 projects have the following limitations:
- Specific filter fields are unavailable in the participants and messages tabs. These filter fields are: Tasks, Manager Tasks, Self Evaluation, Subject’s Metadata, Evaluations, Evaluations Received, Nomination Requirements.
- Deleted participants who have received emails will not be included in the mailing history. As a result, your number of emails sent may not match your number of participants in your project.
- Legacy Admin and Subject reports are disabled. Use the new reporting tool instead.
- Distribution history and message templates are not currently supported.
- Nominations may take more time to load in the Qualtrics platform.
- Workflows: The Run immediatelyoption within Workflows is not compatible with data isolation.
- XM Directory: XM Directory has a few unique Data Isolation limitations:
- XM Directory data stored in a contact field, embedded data field, and the Transactions tab are data isolated (i.e., encrypted with a customer key). No other XM Directory data is data isolated.
- Sorting is not available for directories with Data Isolation enabled.
- XM Discover: Data isolation is available for XM Discover upon request, but please be aware of the following:
- Data isolation is only available for new XM Discover accounts. Existing XM Discover accounts cannot have data isolation enabled for them.
- Some XM Discover data is stored in a separate single tenant database in lieu of encryption with the customer key.
Example Situations
- Unauthorized user gets physical access to Qualtrics database.
- Qualtrics databases are housed in secure, guarded facilities. In the unlikely case that an unauthorized user acquired physical access to a Qualtrics database and extracted the data from the discs, the data would not be readable for a customer using Qualtrics Data Isolation because all of that customer’s data on the drive would still be encrypted with industry standard, secure encryption algorithms.
- Unauthorized user gets physical access to Qualtrics data.
- Qualtrics takes data security seriously. In the unlikely case that data from one Qualtrics customer was made available to another through a hack or error, data from a Data Isolation customer would be illegible to the second customer because the data are all encrypted with a unique customer key. The second customer would simply see the unreadable, encrypted strings.